Literature Review on Positioning, Tracking and Monitoring Systems for Human Kidnapping
Oluwole Charles Akinyokun1, Osagie Kingsley Omoruyi1 and Abejide Michael Adegoke2
1Department of Software Engineering, Federal University of Technology, Nigeria
2Bells University of Technology, Nigeria
Submission: August 16, 2022; Published: September 30, 2022
*Corresponding author: Oluwole Charles Akinyokun, Department of Software Engineering, Federal University of Technology, Nigeria
How to cite this article: Oluwole Charles A, Osagie Kingsley O, Abejide M A. Literature Review on Positioning, Tracking and Monitoring Systems for Human Kidnapping. Trends Tech Sci Res. 2022; 5(4): 555668. DOI: 10.19080/TTSR.2022.05.555668
Abstract
This research opened a window to the methods and materials for positioning, tracking, and monitoring systems for human kidnapping with a view to improving the security awareness of the society. RFID RTLS, GPS, Smart Objects, and Internet of Things are studied and evaluated. The popular existing research work on positioning, tracking, and monitoring of human kidnapping using these tools are examined and evaluated with a view to developing a system for human kidnapping.
Keywords: RFID; RTLS; GPS; Smart object; Internet of things; Positioning; Tracking; Monitoring; Kidnapping
Abbreviation: RTLS: Real Time Locating System; GPS: Global Positioning System; RFID: Radio Frequency Identification; IRID: Infrared Identification; US-ID: Ultrasound Identification; IoT: Internet-of-Things; ESI: Energy Service Interface; PMD: Primary Mobile Device; GDI: Global Device Identifier; AID: Access Identifier; LLOC: Local Locators; GLOC: Global Locators; AGW: Access Gateway; RS: Router Solicitation; RA: Router Advertisement; GNSS: Global Navigation Satellite System; DSR: Digital Station Room; MSS: Media Server Station; SES: Smart Engine Server; ADC: Analogue to Digital Converter; VCS: Video Capture Station; ICTAC: Communication Technology Application Centre; ToA: Time of Arrival; RSSI: Received Signal Strength Indicator; EKF: Extended Kalman Filtering algorithm; GPRS: General Packet Radio Service; UMTS: Universal Mobile Telecommunication Service; LCD: Liquid Crystal Displays
Introduction
Inadequate information available to security agents, lack of operation intelligence and absence of modern tracking equipment are critical challenges bedeviling the crusade against the growing trends of monitoring human kidnapping in the world today. The inability to tell the whereabouts of kidnappers has been a major challenge to investigation because even if the law enforcement agencies are ready for a rescue mission, they do not know where to start. Rather, the traditional random and limited informed search and rescue method were used. Hence, the need for an efficient and effective approach that will aid the law enforcement agencies to carry out a well-informed investigation procedure.
The magnitude at which technology has evolved over recent decades and applied to several sectors has been impressive. Unfortunately, the gains in technological advancement have not truly been felt in the area of positioning, tracking, and monitoring of human kidnapping. The existing methods of combating human kidnapping are susceptible to delays, corruption, and huge loss of funds. The need for effective and efficient system which will adequately address the limitations and vulnerability of the traditional methods has given birth to the development of tracking technology and Real Time Locating System (RTLS).
RTLS has made a positive impact in several industries like retail services, vehicular tracking, hospital management and many others. The ISO standards have defined RTLS as wireless systems with the ability to locate the position of an item anywhere in a defined space at a point in time that is close to real time. The emergence of Smart Objects and Internet-of-Things (IoT) has further expanded the application domain of RTLS. Several technologies that are usually combined to provide RTLS solution are: Global Positioning System (GPS), active and passive Radio Frequency Identification (RFID), Infrared Identification (IRID), Ultrasound Identification (US-ID), Bluetooth, Wireless Local Area Network WLAN, Wi-Fi, and so on.
Smart objects are independent physical or digital objects that in addition to making application logic, they can also sense, process and network with other objects. They make sense of their local environment and interact with human users, sense and interpret what is occurring within themselves and the world, act on their own, intercommunicate with each other and exchange information with people Kortuem et al.,[1]. The objects contain embedded technology to interact with internal states or external environment. Basically, IoT brings together smart objects and wireless connectivity. The GPS is a satellite navigation system that launches into orbit by the USA Department of Defense. Originally, the GPS technology was meant to be used by the military but was later approved by the USA Government to be available for civilian use. The GPS signal contains satellite identity code, current date, current time, and other information sufficient to determine the position of any object in real time. The downside of GPS technology is that it is not efficient in places like underground tunnels, inside of buildings and many other areas where there is no GPS signal from the satellites. Other technologies like RFID can suffice in enclosed regions where GPS signal is limited. RFID can be defined as non-contact automatic identification technique via which an object can be identified using radio frequency and obtain data autonomously. There are basically three components that make up this technology namely: RFID readers, RFID passive and active tags, hardware, and software infrastructures.
The aim of the research is to open the window to the various methods and materials for positioning tracking and monitoring of objects using Smart Objects and Internet of Things with a view to improving the security awareness of the society and also providing data for informative investigation of any missing objects in real time. Many existing research works are reviewed with the aim of knowing their motivations, objectives, method, materials, contributions to knowledge, and limitations.
Literature Review of Some Existing Related Research Work
Ayman [2] developed a wearable tracking system for children kidnapping. The research was motivated by the rising cases of child kidnapping in Egypt. The objectives of the research were to design and develop a wearable tracking system that can communicate with the parents of their children in school via SMS. The author carried out a review of existing works relating to tracking technology. He designed an attractive shoe add-on that is connected to a belt containing a GPS tracking system that can be installed in all kinds of shoes. The research contributed to knowledge in helping to track a child and sending notifications to parents via pre-stored phone numbers in any instance if a child has gone outside a pre-defined perimeter of a school. The research was limited in the following ways:
a) Signal loss in GSM non-coverage areas.
b) There are challenges of sending a real-time coordinate to the parents in cases where there is no signal in the tracking scene.
c) Detailed information on the hardware and software specifications of the developed system was not given.
Pankaj & Bhatia [3] developed a GPS/GSM based tracking system with Google map-based monitoring. The research was motivated by the rising cases of vehicle theft and the need for a low-cost tracking solution than what was presented in existing works. The objectives of the research were to design and develop a tracking system that uses GPS for positioning, GSM for data transmission and Google map for display and monitoring. The system has a single GPS device that will receive the coordinates from the satellites. A two-way communications process was achieved using a GSM modem that is provided with a SIM card. The system architecture consists of a transmitting vehicle unit which comprises of both the GPS device GSM device and the monitoring side. The GPS device is used for receiving the coordinates from the satellite network. The GSM device is used for transmitting and receiving the data. The research suffered the following limitations:
a ) It is very bulky.
b ) GSM was used as transmitting unit and receiving unit; hence it is not an economical solution.
c ) A 9V battery is not able to power the system for long periods, hence there is a need for frequent replacement of the battery.
d ) The system is pre-programmed with a particular phone number as recipient. It fails to offer easy modification of the phone number in cases of change of number or ownership.
Matthews et al.,[4] developed a Covert Kidnapping Alert and Location Identifier (CKALI). The objectives of the research were to:
a) Design a system that incorporates GPS and GSM technologies to improve the limited range of RFID tracking solutions.
b) Develop a functional prototype for real-time tracking of kidnapped victims in order to allow fast response and rescue of kidnapped victims.
The approach adopted by the research was based on the provision and proper translation of location information in terms of latitude and longitude using the GPS/GPRS module connected with a microcontroller and a battery embedded in a belt and having the ability to effectively communicate with the Google Earth Software installed on a computer system via the GSM network, where the location information in latitude and longitude terms were decoded into actual places on the map. The SMS can be triggered by pressing the miniature panic button located on the belt. Machine to Machine (M2M) technologies and GSM/ GPS module were both adopted in the design of this system. The system has the following parts:
a. The first part was the tracking device which was attached to the belt. It comprises of a GPS module, a microcontroller, and a GSM module.
b. The second part of the system consists of a receiver device that receives the GPRMC messages and sends it to the monitoring workstation PC connected to the Internet and running Google Earth and Franson GpsGate client software.
Some of its functions include:
a ) Using JavaScript to gather GPS position.
b ) Normalizing the GPS connection.
c ) GPS simulation and logging.
d ) Sharing one GPS to several applications using virtual communications ports.
e ) Connecting a GPS to Google Earth.
f ) Sending GPS data over HTTP to a personal server.
g ) Multiplexing and splitting NMEA streams.
The software installed on the monitoring system acquired the GPS coordinates reaching the GPS module interfaced with the receiver, logs it continually and connects dynamically with Google Earth to provide a trace of the path of the tracked kidnap victim. The core tracking functionality of the system was done by the Google Earth software. Google Earth is a virtual globe, map and geographical information program that maps the earth by the superimposition of images obtained from the satellite imagery and was able to show all kinds of images overlaid on the surface of the earth and a Web Map Service Client. Figure: 2.1 showed the CKALI signal flow.
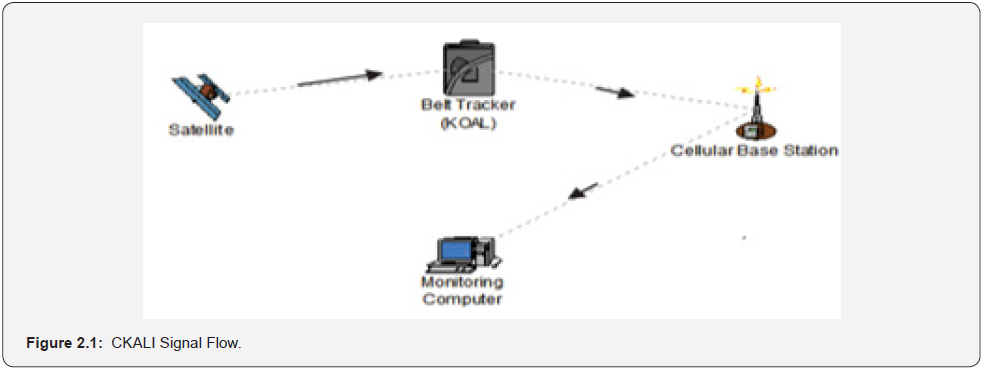
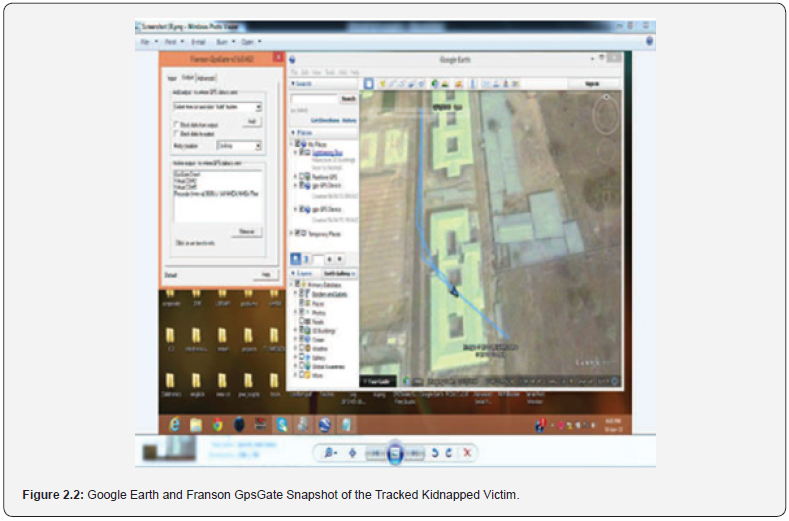
CKALI was tested by setting up a system to simulate a human kidnapping scenario. The belt tracker was worn at each instant by different persons scattered across a geographical area around Ogun state in Nigeria. Each person was told to press the trigger on the belt and then to drive around with the device for twelve minutes, while the authors did the monitoring of the persons location and route from the monitoring computer system. For everyone that wore the belt in the various locations when the trigger on the belt was pressed, the GPS module retrieved the location information from satellites in the form of longitude and latitude real time readings. This GPS information was then processed and sent by the microcontroller as an SMS through the GSM network using the GSM module to the alert pre-configured phone and the GSM modem of the monitoring system. The authors were alerted by the SMS reaching the phone. The SMS message received was: “help! i have been abducted. Please start tracking”. The GSM modem on the monitoring system also received the SMS which included the GPS coordinates of the individual wearing the belt. A total of 18 messages were sent by the belt tracker device during the 12 minutes duration. The authors reported that the Longitude and Latitude readings were accurate and reflected the exact location of the individual wearing the belt and were able to trace the route of the individual. The route taken by the individual wearing the belt tracker as received in the monitoring system is shown in Figure: 2.2.
The limitations of the research where the delivery of the SMS messages was network dependent, thus a reliable GSM network connection is needed to improve the effectiveness of the devices, the belt on which the device is worn is more inclined to the male gender whose clothing goes more with a belt. The victim may not have the opportunity to press the trigger that activates the monitoring system. The research contributed to knowledge in the following ways:
a. It presented a miniaturized solution to combating human kidnapping.
b. It presented a tracking solution for combating human kidnapping that covers more range than an RFID tracking solution.
Akintola et al.,[5] developed a face detection and recognition in real time video surveillance. The research was motivated by the growing trend of emerging smart visual surveillance systems requiring automatic detection and recognition of human beings within the scene and the prediction of the actions being performed by the detected human objects. The objectives of the research were to:
a. Design a framework for the automatic detection and recognition of human beings in video cameras via smart visual systems that automatically sense and recognize human identity and actions by means of machine vision techniques.
b. Implement the framework in (a).
c. Carry out the evaluation of the system with existing research works.
The paper reviewed some existing research systems for human identification using video signals which were specially designed for use in facility access control. It designed a framework for a face detection and recognition in real time video surveillance with a preprocessing stage based on a rapid frontal face detection system using Haar-like features introduced by Viola et al., (2001). The face recognition system was based on the eigenfaces method introduced by Turk et al., (1991). Eigenvector-based methods were used to extract low-dimensional subspaces which tend to simplify tasks such as classification.
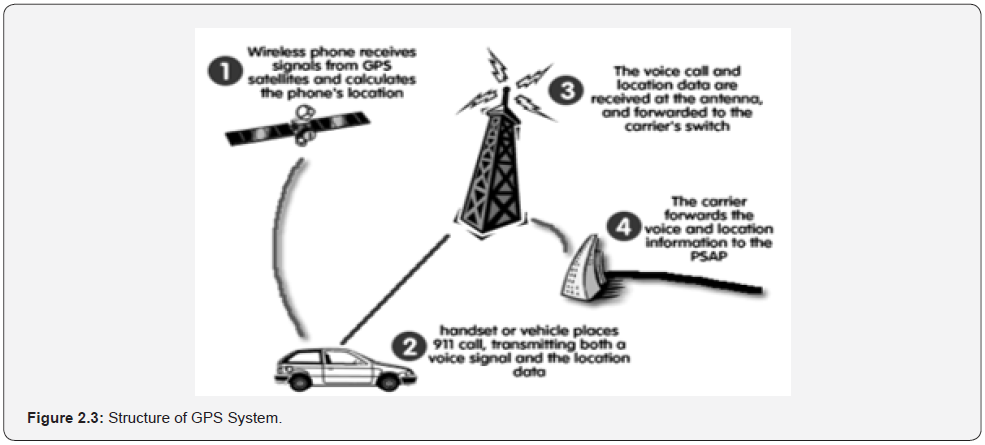
Sungur et al. [6] developed vehicles identification and positioning system. The system was motivated by the need to create alternative systems that can address the expensive and limited nature of GPS systems. The system is composed of twentyfour satellites which continuously move in orbit and broadcast very low-power radio signals. The GPS receiver on the earth surface makes it possible to determine the definite position on the earth by receiving the radio signals and measuring the distance from the satellites. The function of the GPS is presented in Figure: 2.3.
The structure of the GPS system is composed of three major parts, namely: the space segment, the control segment, and the user segment. The space segment consists of at least twenty-one active satellites and three on-orbit spares. Each of the satellites transmits radio signals on two different frequencies. Civilian GPS satellite signals are transmitted at a frequency of 1575.42MHz in the UHF band while military GPS signals are transmitted at a frequency of 1227.6 MHz and are used by the US defense unit. In the research, the authors used an ATX-34 circuit as the RF transmitter and an ARX-34 circuit was used as the RF receiver. ATX-34 and ARX-34 circuits were preferred for their high stability and wide area of use. The circuits comply with the radio standard EN 300 200 at 433.920MHz UHF band, have high frequency stability and were ideal for battery applications with low current consumption. The authors utilized the PIC16F877 microcontroller manufactured by Microchip Technology Incorporation for entering the license plate information of the vehicles, programming and storing the information coming from the transmitter.
The microcontroller was programmed using a different programming language. The antenna used in the study had an impedance of 50 Ohms and was approximately 17.3cm. The transmitter circuit was programmed together with the license plate information. The PIC16F87 integrated circuit can be locked against rewriting and reading during the programming process. In this way, the access of unauthorized persons to the license plate information of vehicles can be restricted. Two transmitter and one receiver circuits were used in the system design. The receiver circuit was located at a point on the route determined for the study. The two transmitters were placed on two different vehicles. The vehicle information of each vehicle passing along the route is read by the RF receiver. In this way, it was known which city the vehicle was traveling to, where it stops over and from which direction the vehicle enters the city. An area on which the license plate information of the searched vehicles can be entered was added to the computer software used for recording and monitoring vehicle information. In this way, when the sought vehicle entered the coverage area of the receiver, the vehicle information was delivered to the system user through the computer. The authors reported a total of five experiments were conducted; the distance required for the recognition of the vehicles equipped with a transmitter by the receiver, the speed of the vehicle, which was effective on recognition, weather conditions, the effect of the position of the receiver and the transmitter on the recognition of the vehicle. The paper contributed to knowledge by developing a tracking solution that does not utilize global satellites and is less expensive. However, it was observed that the performance of the system decreases when the experiments were performed under maximum conditions, that is, under very heavy traffic and unfavorable weather conditions.
Chaudhari et al.,[7] developed GPS/GSM enabled person tracking system. The research was motivated by the high cost of tracking based on GPS. The objectives of the research were to reduce the overall cost of tracking system based on GPS. Some literature reviews were carried out by the authors revealing the following three main methods used for tracking:
a ) Automotive navigation system for tracking automobiles.
b ) GPSylon used to enable maps which can be downloaded from Expedia Maps Server.
c ) Open GTS which provides web-based GPS tracking system.
In the research, GPS was used to monitor a person location anywhere on earth. The carrier must have GSM modem with SIM GPRS enabled. The GPS consists of GPS Transmitter and GPS Receiver. The GPS unit simply measures the travel time of the signals transmitted from the satellites, then multiplies them by the speed of light to determine exactly how far the unit was from every satellite it was sampling. By locking onto the signals from a minimum of three different satellites, a GPS receiver could calculate a two-dimensional positional fix, consisting of latitude and longitude. The GPS receiver was interfaced with an ARM through RS232 converter. RS232 converter was used to convert RS232 logic to TTL logic and vice versa because the GPS receiver used is on RS232 logic while the ARM-7 is on the TTL logic. The receiver sent the received signal to ARM-7. The ARM-7 is the flash type programmable ARM that was earlier programmed by the authors. The ARM-7 displays the person location on an LCD display. This same position information was transmitted through a GSM network whereby the person could be remotely tracked. The research contributed to knowledge a low-cost tracking device based on GPS and GSM. The system developed was very bulky and there was no real-time tracking of persons.
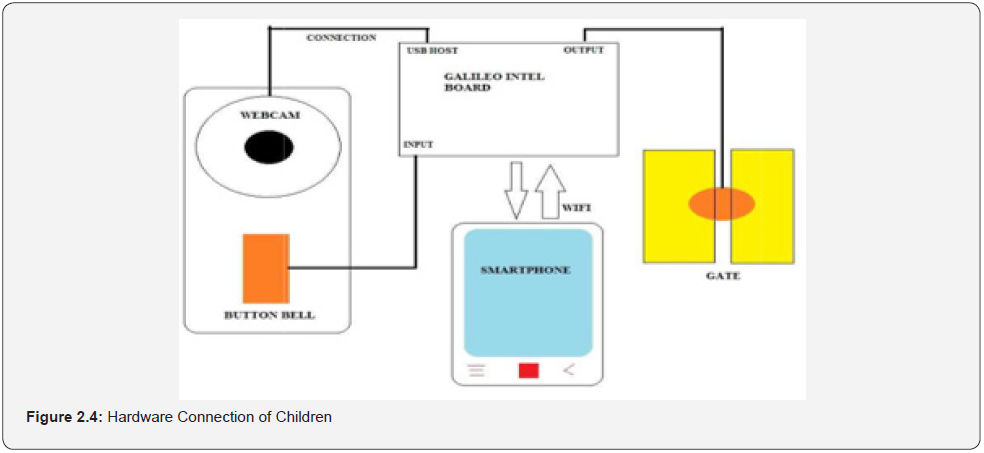
Hadi et al.,[8] developed a prevention system for child abduction by using image processing algorithm on Intel Galileo Board. The research was motivated by the growing abduction cases and the need to reduce children abduction. The objectives of the research were to develop a flexible and cost-effective system that operates an access control for a school in order to improve the security of the children within the school premises. The authors carried out an extensive literature review on several models on face recognition. A webcam and OpenCV software were used in the face recognition experiment. OpenCV software is an open-source library developed by Intel and includes many real time computer vision algorithms focused on real-time image processing. The webcam utilized the OpenCV software to detect and calculate the centre X and Y coordinate of the face. The system architecture is shown in Figure: 2.4. Abduction prevention system via face recognition algorithm on Galileo Intel Board attempted face recognition and upon failure in recognition, the system will make a video call to the owner of the school by Wi-Fi. Otherwise, the system will detect the visitor’s blinking eye. When eye blinking is detected, the system unlocks the gate. If there is no blinking eye detection, the system will send an alarm to a pre-defined smart phone. The eye blinks ensure that the webcam detects a face instead of a picture. Intel Galileo Board was used as the main processor to control all signal and input and output data. The board can receive data from other devices, store and send the data to another device. The research suffered a limitation as a real-time notification to the owner of the school was heavily reliant on the reliability of the WIFI network available at the premises. Any downtime or failure on this node would prevent timely notification to the owner.
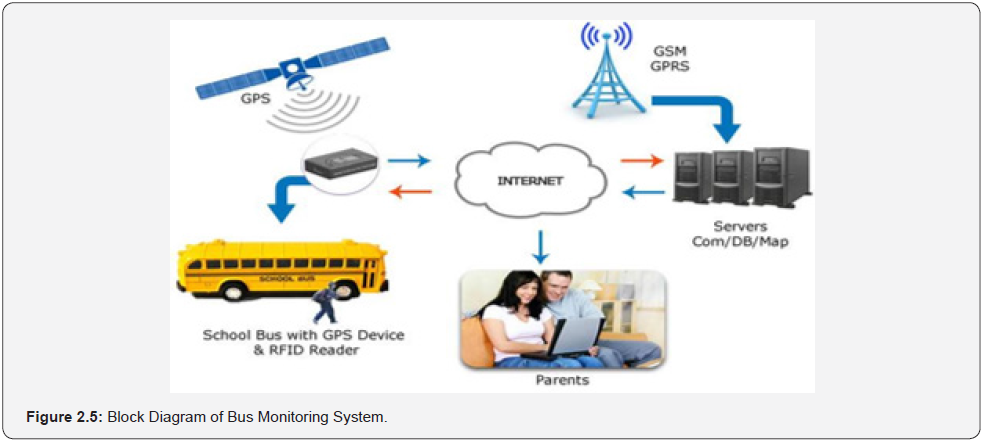
Dukare et al.,[9] developed a vehicle tracking, monitoring and alerting system. The authors carried out an extensive literature review on tracking, monitoring, and alerting of vehicle (car, truck, cargo, bus, and bike). The car and bike needed the system to know the real time location of car and bike for safety purpose and to avoid theft of vehicle and alert the owner. The cargo used real time tracking and monitoring system. Real time tracking of bus involved, monitoring passenger in the bus, predict arrival time and send information to the base station. The public transportation uses tracking and monitoring of the bus for arrival time prediction of bus to the various bus stops. The block diagram of bus monitoring system is shown in Figure: 2.5. The authors carried out a comparative study among existing systems and showed the comparison of existing systems based on parameter used. In bus transportation system, WSN improves transportation system performance, but the problem is short range of transmission information. In children tracking system, the system had limited functions such as the size of student module is big, and this limits its use. In public transport management system, the circuitry is complex and costly. The research was, however not developed for ready evaluation.
Ahmad et al.,[10] developed context-aware mobile sensors for sensing discrete events in smart environment. The research was motivated by:
a ) The difficulty in providing best facilities in a real-time environment due to high cost of home appliances.
b ) The complex rule sets that exist in traditional wireless sensor and actuator network cannot be directly applied to smart building systems.
c ) The absence of a unique platform for exchange of information between varieties of devices which are heterogeneous in nature.
d ) Several challenges of power, communications and sensors connectivity distort the inter connectivity between different technologies such as Bluetooth and ZigBee.
e ) The lack of focus given to the Energy Service Interface (ESI) by earlier research work which is considered as the main communication gateway for a smart building.
The objectives of the research were to:
a) Propose the concept of smart building based on embedded systems that enhance low power mobile sensors for sensing discrete events in embedded systems.
b) Propose a system architecture that welcomes all the mobile sensors to communicate with each other using a single platform service.
c) Define a communication model that provides a common medium of communications for low power mobile sensors.
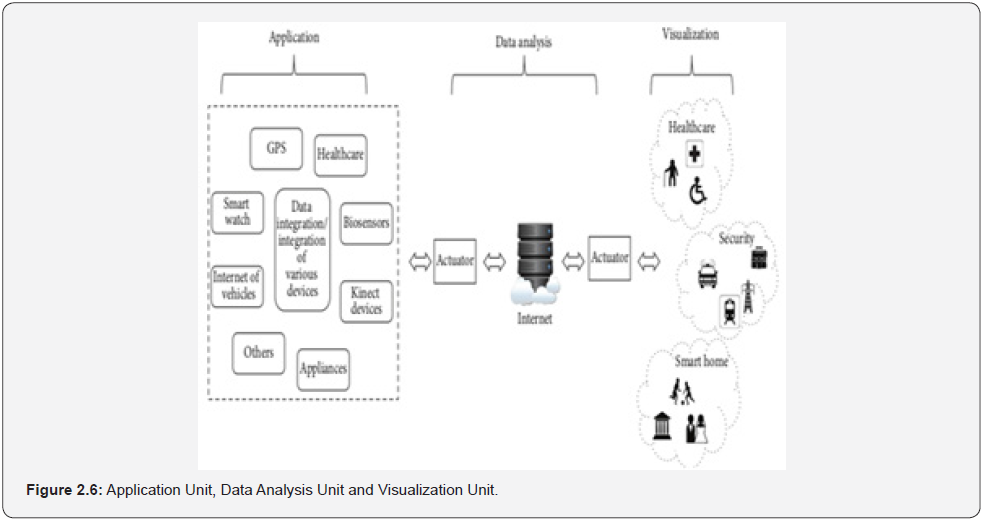
The proposed context-aware low power mobile sensors for sensing discrete events in embedded systems consists of three major units namely: application unit, data analysis unit and visualization unit as shown in Figure: 2.6. The application unit was comprised of the healthcare system, home security system and smart building system. In the healthcare system, the authors employed source identity/location-based 6LoWPAN wireless body area network mobility management scheme. In the architecture, a group of 6LoWPAN sensors attached to human body are considered. In this group of sensors, there is one coordinator that is used for exchanging control messages with Primary Mobile Device (PMD). Each PMD and sensor has a 128-bit Global Device Identifier (GDID). GDID establishes end to end communications provided with the link-layer addresses as the Access Identifier (AID). The GDID has the information about its home domain. The Local Locators (LLOC) and Global LOCators (GLOC) identify location of PMDs within home domain since the GLOC denotes the IP address of Access Gateway (AGW) that is used for inter-domain communication. In the given scenario, each AGW contains home GDID and visitor GDID register. The Home GDID Register (HGR) contains the mapping information about the GDID-LOC and VGR contains GDID-LLOC mapping information for the visited PMDs.
In the authors proposed architecture, the only one-time Router Solicitation (RS) and Router Advertisement (RA) messages are sent by the coordinator and thus reduce lots of control messages. Initially, the PMD communicates with correspondent PMD (C-PMD) in the previous AGW (p-AGW) domain. The PMD moves to a new AGW (n-AGW). Finally, the proposed smart building is equipped with the electronic appliances which are interconnected with each other with the help of Bluetooth and ZigBee technologies. The proposed architecture is composed of different embedded devices such as mobile sensors, healthcare system and security system located in a large geographic area. The embedded deices are deployed in home, police station and fire and brigade centers.
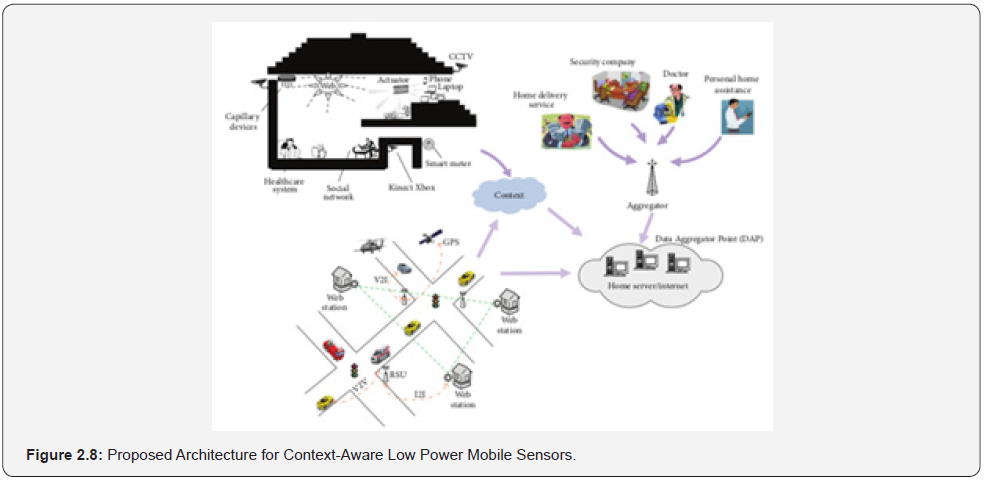
These devices are interconnected with each other with the help of Internet using short range communication technologies like Bluetooth and ZigBee technologies such as WLAN and cellular as shown in (Figure: 2.8). where different electric appliances are interconnected with the help of the Internet. These appliances are also connected with the home server that helps in storing the data for analysis purposes. All the electric appliances are controlled remotely. The research contributed to knowledge in the following ways:

a ) An architecture that significantly reduced the energy consumption of sensors in a smart home network was proposed.
b ) A communication model that resolves the heterogeneity bottleneck that hinders interconnectivity between varieties of devices was proposed.
However, the research was limited in that there is a high reliance of the architecture on cellular technology for contacting relevant department in emergency scenarios. Connectivity failure on the cellular module can prevent timely and critical notification from reaching the relevant department.
Du et al.,[11] developed tag location method integrating GNSS and RFID technology. The research was motivated by:
a. The need to provide an improved positioning accuracy required for outdoor positioning with a rapid and accurate locating of target objects, which is very helpful for specific objects positioning and change detection in daily urban management and regulations.
b. The need to combat the challenges of weak signal availability in urban areas which is peculiar with Global Navigation Satellite System (GNSS).
c. The challenges in locating movable urban management components rapidly and effectively by urban management administrator.
d. The costly and impractical RFID solutions for big city.
The objectives of the research were to develop a vehicle inspection and supervision system and evaluate the system developed. The authors presented a comprehensive review of the trends on location technologies covering GNSS, GPS and RFID technologies. The research proposed a novel tag positioning method based on GNSS and RFID. The location device was composed of GNSS and RFID reader which were mounted on vehicle. The GNSS provided the vehicle position. The RFID reader can get the distance to target RFID tags. Based on the vehicle coordinate and distance, the target tags can be located. The device consists of vehicle GNSS module and RFID module. The former is responsible for the real-time positioning of the RFID reader. It includes GNSS receiving antenna, GNSS chips, GNSS software. The later module is employed to capture the signals of RFID reader and RFID tags and then to calculate distance location algorithm: The principle of the proposed algorithm is simulating of the radio frequency station network by rapid movable RFID readers. An RFID tag was equipped on the target points. The RFID reader received the tag’s signal continuously when the vehicle is moving within the ranging distance so that distance between RFID reader and tag can be calculated. The location of RFID reader is gotten by the vehicle GNSS. Based on the distance and RFID reader coordinate the target tags can be located.
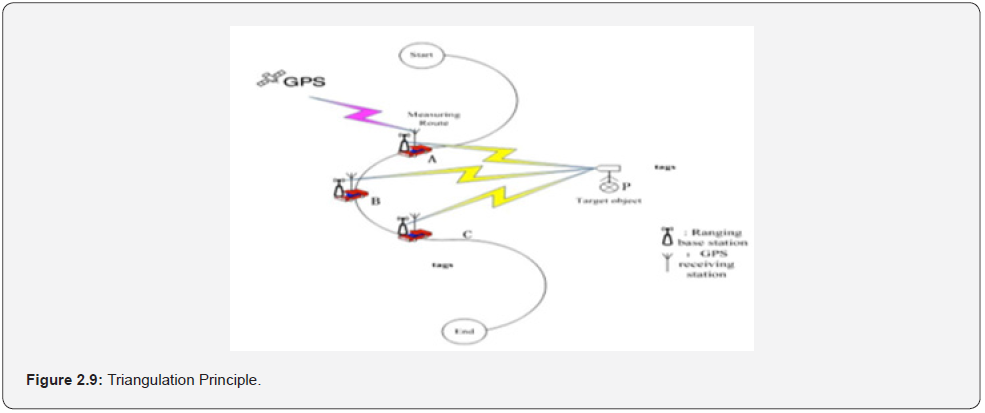
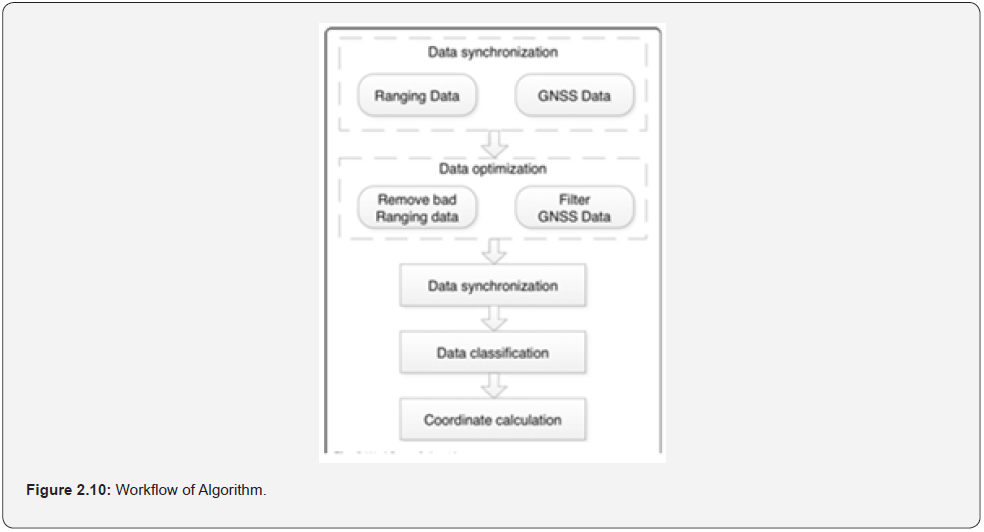
The principle was based on the theory of “triangulation” shown in Figure: 2.9, where A, B and C are three different points for the movable RFID readers respectively, called ranging points; P is the target object, which is equipped with target tag, called target tag. Figure: 2.10 showed the detailed workflow of the algorithm. The detailed workflow of algorithm includes the following five steps:
a. Data capture including both GNSS and RFID data when vehicle is moving.
b. Data optimization includes filtering bad ranging points data and GNSS data.
c. Data synchronization for ranging points and GNSS points based on time.
d. Data classification with specific ID is assigned to the corresponding target tag.
e. Target tag’ coordinate calculation based on more than 3 ranging points.
Data optimization and coordinate calculations are also carried out in the location determination process.
The research contributed to knowledge in the following ways:
a ) A comprehensive literature review on RFID, tagging and location methods was carried out.
b ) A vehicle inspection and supervision system were developed.
c ) A positioning algorithm was presented by combining vehicle Global Navigation Satellites System (GNSS) and mobile RFID readers.
d ) The positioning accuracy of less than 5m within 160m was achieved in this design, such that the system was good enough for the management of the breakfast vendors, newsstands, billboards, and other urban management case studies, which provides a new convenient and accurate approach for the urban supervision and management.
The research was limited in that the multiplicity of readers presents an added cost to the implementation.
Akinyokun et al., [12] proposed a framework for combating human trafficking and human kidnapping using smart objects and Internet of things. The research was motivated by the following:
a) High rate of human kidnapping and human trafficking which has attained global dimension and has defied several measures adopted by governments and organizations.
b) The advancement and complexity of the present-day society which has made most of the crimes to go online and hightech in nature, hence the need for matching strategies.
c) The use of human personnel for surveillance has been ineffective and susceptible.
The general objective is to develop a system for combating human kidnapping in Ondo State of Nigeria. The specific objectives are to:
a. Carry out baseline study of human kidnapping in Nigeria and develop its national dataset.
b. Design a Smart Objects, Internet-of Things, and whistle blower model for combating human kidnapping in On-do State.
c. Design all-inclusive national dataset on human kidnapping in Nigeria
d. Implement the models designed in (b) and (c)
e. Perform experimental study of the models based on the results in (d).
In order to accomplish the objectives of the research, the authors carried out an extensive review of previous research works on RFID, GPS, Smart Objects and IoT. The proposed framework has two phases namely: hardware operational requirements phase and software analytic framework phase.
The authors have developed standard platforms for offline scanning and forensic analysis of biometrics of individuals, video surveillance and human resource monitoring in the workplace. The gaps between the existing research works and the proposed one in this study are the real time forensic analysis of biometrics of kidnappers, video surveillance of kidnappers and human resource activities, location and movements monitoring outside workplace using hybridized Smart Objects, Internet-of Things, RFID tags/ readers, GPS modules, sensors, and other related technologies towards combating human kidnapping in Ondo State of Nigeria. The authors have developed adaptive video analytic framework for real-time human monitoring in workplace, but with very limited operational range. They have also developed a fingerprint recognition system which only operates in offline mode and a hybrid system for human resource monitoring of the activities and movements in the workplace which gives no considerations to individuals with unknown identities. Though, there is evidence of substantial preliminary works on the research domain, the issue of identifying and tracking kidnappers has not been addressed. The aforementioned limitations imply that the reported works are not suitable for providing lasting solution to the prevailing problem of human kidnapping. Further challenges to addressing the problem of human kidnapping include lack of national dataset as well as absence of scientific and standard techniques for combating it.
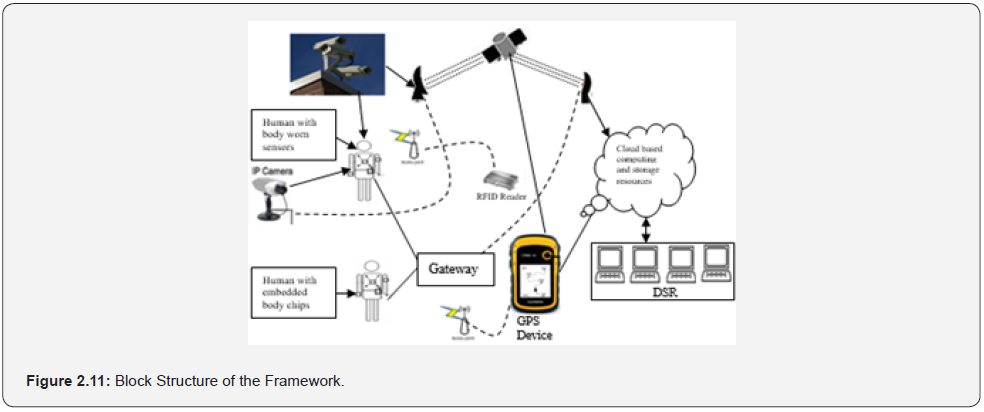
The theoretical framework is the Sigmund theory of psychodynamic factors which include unemployment, political, social, and economic instability which according to the authors, improper handling of these factors renders the society insecure. The system employs Internet of Things wearable devices which are made up of Arduino Uno microcontroller, wireless RFID tags/ readers and GPS modules. Hardware Operation Requirements Phase which has four stations. First, is the Sensor Processing Stations (SPS) which has workstations equipped with video camera sensors, RFID tags, GPS receivers and body worn sensors. Video camera sensors captures the video data of the area being monitored, A non-digital camera embedded into a broach type model attached to buttons or human hair for taking and forwarding real time pictures to the Digital Station Room (DSR). RFID tags monitors objects indoor while GPS handle global monitoring outdoor. The SPS has ID cards carrying chips embedded in the skin, wrist bands, button or hair of individuals for checkpoints identification of carriers. Second, the captured data are stored in the cloud-based Media Server Station (MSS). Third, the Smart Engine Server (SES) located in the cloud handles motion detection, face recognition, position tracking and activities recognition. The Digital Situation Room (DSR) monitors events in real time and on demand based on RFID tags and embedded communication protocols version chips. The Internet protocols version is selected for addressing scheme for data transfer on the web. The Non- Visual Module (NVM) comprises IoT objects, RFID sensors and GPS that are for signal and location. The Video Capture Station (VCS) has digital cameras and software for sensing, digitizing and compressing video cameras. There is visual monitoring subsystem, which make use of Internet as communication medium. Video data captured in monitored area is sent to video captured adapter board attached to the system. On the video capture adapter card, an Analogue to Digital Converter (ADC) chip converts the wavering analogue video and audio signals to a pattern of 0s and 1s. The Internet will be used as the communication framework for real time video transmission to remote locations. The Digital Situation Room (DSR) will be used to view the raw video files after they have been stored in the server. Each video playback station will have playback client software based on Microsoft media player.
Software Analytic Framework Phase which consists of following modules for object location detection and tracking using RFID analyzer, face recognition and activity recognition.
a ) Video Analyzer:
The system cameras will capture images of the scene and will record it in a video storage device or passed to the next modules for analysis. Identity recognition and intrusion detection will then be carried out using video analysis module. After a kidnapping scenario is detected by the system, human detection, classification and tracking operations will follow, features will then be extracted from the face and the whole body. The extracted facial features will be passed to the face recognition module while the features from the whole body will be passed to the activity recognition module. The extracted set of features will also be used to identify intraders. The activity recognition module is responsible for action segmentation and recognition. These modules generate different alerts which are stored in the database for subsequent retrieval or viewing. It is noted that face and activity analysis modules can be executed in parallel.
b ) GPS Analyzer:
The GPS is for global location and tracking. For outdoor surveillance, human beings will be equipped with GPS receiver sand the location of the user will be tracked continuously. Obtained information will be sent to the DSR and in case the location is outrageous; an alert will be generated as acknowledgement to the remote user for onward transmission to the law enforcement agents for necessary action. In case of removal of the devices from the user, an instantaneous alert will also be sent.
c ) RFID Analyzer:
The RFID will be used for indoor localization. For indoor surveillance, human beings will be equipped with wireless wearable sensors and RFID tags. While indoor and with the help of wireless sensor networks, the location of the user in the environment will be tracked continuously. This information will be sent through GSM to remote stations that are monitoring the objects. If the allowed radius of movement is exceeded, an alert will be generated and sent to the remote user while a short video stream of the previous durations will be sent to the remote user for transmission to the law enforcement agents for necessary action.
d ) Sensor Analyzer:
This will be used to analyze and connect other sensors such as infrared sensors, motion sensors, ultrasonic sensors, laser sensors and buzzer to the tracking system.
Adewole & Akinyokun, [16]. developed hybrid human resource’s location and monitoring system. The objectives of the research were to:
a ) Design a multi-sensor and heterogeneous localization and positioning model for boundless monitoring of human resources.
b ) Implement the model designed in (a).
c ) Carry out the case study of monitoring of human resource of Information and Communication Technology Application Centre (ICTAC) of Adekunle Ajasin University, Akungba-Akoko, Nigeria.
The authors carried out a review of relevant literature on the fundamental concepts of human resource, RTLS, IoT, GPS, RFID, digital and future workplace paradigms. The proposed system has three sub-systems: namely database, data generation and hybrid location engine.
a ) The database subsystem dealt with the creation of databases for human resource, electronic devices, buildings and landmarks.
b ) The data generation subsystem uses GPS, RFID, camera and sensors to obtain human resource, device or building positioning data. The estimation of positioning data in indoor environment is based on hybridization of Time of Arrival (ToA) and Received Signal Strength Indicator (RSSI) distance estimation techniques. In ToA technique, the distance α between the HR and the reader in a direct Line of Sight (LOS) environment is obtained based on the formula:

where v is the velocity of the signal, t is the time spent by the signal travelling from the reader to tag. In a non-LOS environment, RSSI estimation technique was used based on the signal strength of the transmission between the reader and the tag which is converted to distance by using the Euclidean equation as follows:

where d represents the distance between the reference tag and unknown tag, qi is the signal strength of the reference tag, pi is the signal strength of the unknown tag received on the reader and n is the number of times measurement is taken. The physical location of the tag was obtained from the measurement of distances by using Trilateration method which is expressed as follows:
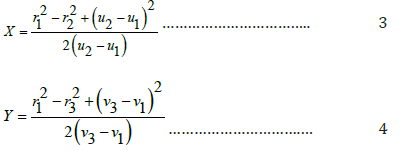
r1, r2 and r3 are the distances of the unknown tag from the reference positions A (u1, v1), B (u2, v2) and C (u3, v3) respectively. The author utilized GPS in outdoor environment. The general model for calculating the position of a user, p, relatively to the transmitting satellite is expressed as:

where c is the speed of light, tj is the user time offset with respect to jth GPS system time, tk is the auto-correlation sequence at kth time. In cases where access to all the satellites in the same orbit at the same time is not possible, satellite from other orbits is used and the pseudo-range distance of the unknown mobile GPS receiver coordinate (xm, ym, zm) evaluated on the basis of the message coming from the ith satellite with clock bias bm and composite error is expressed as:
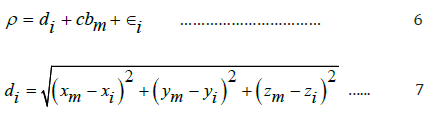
Proximity sensors were used for signal-denied areas and visual images were captured by IP cameras with face recognition feature. The hybrid location engine subsystem combines and fuses the heterogeneous measurements GPS, RFID, camera, and sensor together by using Extended Kalman Filtering (EKF) algorithm. The processes involved in the subsystem were location information reading, measurements reading and position estimation. The author implemented the model using Python programming language as front-end and MySQL database management system as backend on Windows 10 professional. The case study of the monitoring of selected staff of Information and Communication Technology Application Centre (ICTAC) unit of Adekunle Ajasin University, Akungba-Akoko was used to test the adequacy and practical functions of the model. The report obtained on positioning accuracy, cost of deployment, signal sensitivity and coverage formed the basis of evaluation and comparative analysis. The conceptual diagram of the architecture of the system is shown in Figure: 2.12.
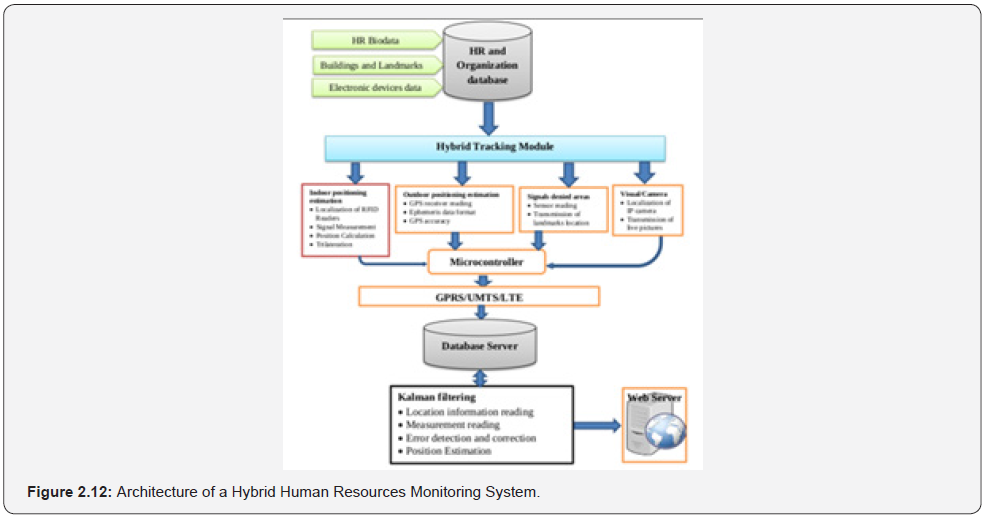
The system comprises of the database, localization, and positioning data generation as well as positioning and hybrid location engine sub-systems. The database subsystem deals with the creation of the human resources personnel record, enumeration of organization buildings, important landmarks, and the mapping of the entire research area. It also comprises of the technical specifications and assigned locations of RFID readers, IP cameras, hybrid tracking module, fixed and movable sensors, reference tags, GPS modules and all electronic devices used for the research. The monitoring and localization subsystem deals with the generation of heterogeneous positioning data depending on the environment by hybrid tracking module. The author noted that due to the autonomous nature of tracking module, it has facilities to switch to either GPS or RFID mode depending on the environment it is operating. The activities involved in this subsystem include the generation of location data from the indoor and outdoor positioning estimations, the signal denied areas which are referred to as landmarks and the visual images captured by the camera. These data were aggregated by the microcontroller and the output was sent to the positioning and decision-making subsystem using General Packet Radio Service (GPRS) and Universal Mobile Telecommunication Service (UMTS). The positioning and decision-making subsystem hybridize readings obtained in the second subsystem by using Kalman filtering algorithm, error detection and correction, optimization of results and updating of the application database for online display. The authors employed a relational database management system for the creation of the database to interrelation between the various entities.
A case study of monitoring of the movements of twenty-five (25) randomly selected personnel of the ICTAC was carried out. The author reported that the study was carried out during the working days and hours between July 1, 2018, and September 30, 2018. During this period, each of the selected personnel received the tracking module and they were mandated to wear it. The authors evaluated major requirements of the localization system such as sensitivity, accuracy, cost, and coverage. The ability of the system to adjust within the shortest time frame to the minutest change in location was highly essential and it formed one of the metrics used in evaluating the system. It was reported that several experiments were conducted to evaluate the developed system using the above stated performance metrics. Since the research was designed to cover both indoor and outdoor environments, the author deemed it fit to evaluate the system taking cognizance of the two environments involved and the technology adopted for each of them.
Experimental results for signal sensitivity, proper reader antenna location and strength, localization accuracy, cost of deployment and scalability and coverage area were presented by the author. Empirical and graphical results of the ability of the system to provide record of availability of personnel at work and measurement of punctuality at work were also presented. Finally, the results obtained in the research work were compared with other existing systems. The comparisons were based on the environment where they were deployed, that is, either indoor or outdoor and the metrics considered were technologies used, algorithm, accuracy, complexity, scalability, robustness, and cost. The research contributed to knowledge in the following ways:
a ) A rich literature on localization and positioning systems was presented in the research.
b ) The research established a multi-sensor localization and positioning model for effective localization, monitoring, objective assessment, and utilization of HR in the workplace.
However, the research suffers the following limitations:
a. The area covered by the indoor equipment was small and only one reader was used per building, hence the effect of signal interference and path loss was not investigated.
b. Due to the type of topography and structures available in the Testbed which were mostly bungalows, the effects of signal diffraction usually associated with high-rise buildings and skyscrapers could not be investigated.
c. An effective and low-cost solution for a more reliable identification of personnel in areas where there are no GPS signals, RFID readers or Camera was not provided.
Poonkodi et al., [17-30] developed an Internet of Things (IoT) based Smart Object Tracking System. The research was motivated by the need to improve airport security and hasten the retrieval of passengers’ luggage. The objectives of the research were to:
a) Study the basic operation of RFID reader and design of the authenticated person accessing system.
b) Optimize the luggage tracking at airports.
c) Design alert system using GSM system by sending realtime luggage information.
d) Design SD card storage memory and interfacing with PC.
The proposed system used RFID (Radio Frequency Identification) technology. The authors implemented passive RFID for luggage identification. An RFID card with unique number and passenger details was attached to every luggage. The unique number is given to the passenger at the entrance of the airport. The RFID tag makes communication with the RFID reader at each stage, informs the luggage details to the user through SMS using GSM modem and the same information was then passed to a database. The authors designed a prototype for two locations having both check-in and check-out processes. At check-in process, each passenger information is stored in the database. The information consists of four important items including the name of airline, flight number, bag nature and mobile number of the passenger along with the identification number which is peculiar to each other. The same identification number is sent to passenger through SMS to keep it personal. When the passenger places the luggage on the conveyor, the reader collects the tag data and records from the beginning of the trip. As the bag moves through the conveyor, the RFID keeps track of the luggage to make sure that the luggage would be delivered to the right gate and flight. At the same time, the database processes the data sent by the RFID system and retrieves from it the passenger’s information to know the unique identification number and send the proper message. When the passenger’s luggage loads into the plane, the passenger receives a message that “Your luggage is loaded successfully.” Same identification number can be used while collecting bag at checkout counters. This ensures less consumption of time, security for luggage and it is economical hence provides customer satisfaction. The hardware component Figure: 2.13 showed the architecture of their proposed luggage tracking process.
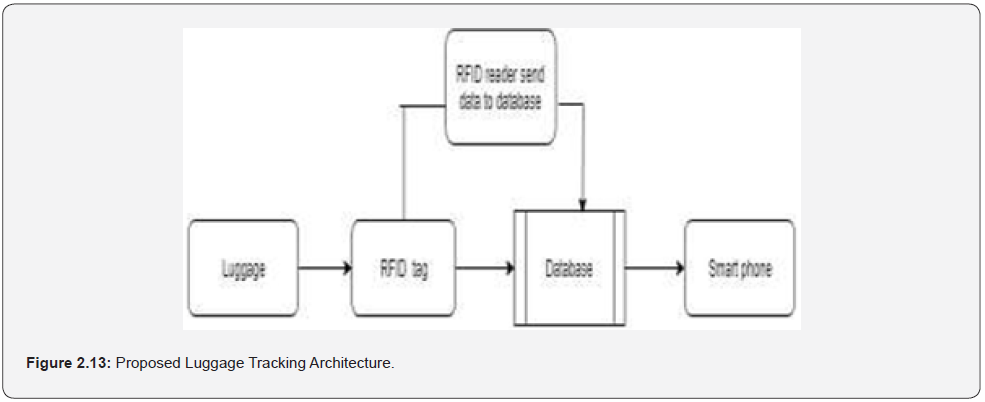
The hardware components used for the development are Arduino Uno R3 micro controller board using ATmega328 AVR, SIM900 GSM/GPRS module, RFID cards, RFID readers and Liquid Crystal Displays (LCD). The research contributed to knowledge by designing a Smart Object Tracking System based on RFID technology that provides an efficient solution for tracking luggage to lower luggage-handling errors and misplacing of luggage at the airports.
Conclusion
The paper reviewed some popular existing research works on human kidnapping with a view to clearly and unambiguously knowing the methods and materials used. The strengths, opportunities and weaknesses of the different approaches were clearly understood and appropriately harnessed and considered essential ingredients to the development of a novel system for combating human kidnapping in the future research paper that the authors are considering.
References
- Kortuem G, Kawsar F, Fitton D, Sundramoorthy V (2010) Smart Objects as Building Blocks for the Internet of Things. IEEE Internet Computing 14(1): 44-51.
- Ayman MA (2013) Using of Tracking Systems for Devices Designing to Face Children Kidnapping Phenomenon (GSM-GPRS-GPS). International Journal of Scientific and Research Publications 3(10):1-5.
- Pankaj V & Bhatia JS (2013) Design and Development of GPS-GSM Based Tracking System with Google Map Based Monitoring. International Journal of Computer Science, Engineering and Applications 3(3).
- Matthews VO, Osafehinti S, Adetiba E, Dike Ike, John SN (2013) A Covert Kidnapping Alert and Location Identifier (CKALI). International Journal of Innovative Technology and Creative Engineering 3(12): 1-11.
- Akintola KG, Boyinbode OK (2011) The Place of Emerging RFID Technology in National Security and Development. International Journal of Smart Home 5(2):37-44.
- Sungur C, Gokgunduz HB, Altun AA (2014) Road Vehicles Identification and Positioning System. 2014 Federated Conference on Computer Science and Information Systems 1353-1359.
- Chaudhari A, Bohra S, Karma H, Dhupadale A (2015) GPS/GSM Enabled Person Tracking System. International Journal of Innovative Research in Science, Engineering and Technology 4(3): 981-986.
- Hadi NHB, Saleh HBM, Asi SBM (2015) Prevention System for Child Abduction by using Image Processing Algorithm on Intel Galileo Board. Journal of Electrical and Electronics Engineering (JEEE) 5 (2):1-8.
- Dukare SS, Patil DA, Rane KP (2015) Vehicle Tracking, Monitoring and Alerting System: A Review. Journal of Computer Applications 119(10): 39-44.
- Ahmad A, Rathore M, Paul A, Hong W, Seo H (2016) Context-Aware Mobile Sensors for Sensing Discrete Events in Smart Environment. Journal of Sensors.
- Du M, Jing C, Du M (2016) Tag Location Method Integrating GNSS and RFID Technology. Journal of Global Positioning Systems 14(2).
- Akinyokun OC, Akintola KG, Iwasokun GB, Angaye CO, Arekete SA (2018) Design of a Framework for Combating Human Trafficking and Kidnapping using Smart Objects and Internet-of-Things. International Journal of Artificial Intelligence Research 7(1): 45-52.
- Awolusi AB (2015)Development of Online System for Monitoring of Personnel in Public Service. Federal University of Technology.
- Akinyokun OC, Adewole DB (2018) Monitoring of Human Resources in the Workplace. International Journal of Current Advanced Research 7(7): 14215-14222.
- Adewole AB (2019) Development of a Hybrid Human Resources Location Monitoring System. PhD Thesis, Department of Computer Science, Federal University of Technology.
- Adewole DB, Akinyokun OC, Iwasokun GB (2019) Hybrid Human Resources Localization and Tracking System. International Journal of Artificial Intelligence Research 8(1): 1-13.
- Poonkodi R, Devaki E, Karthika M (2019) Internet of Things Based Smart Object Tracking System. IRJET 6(2): 929-932.
- Rozyev A, Hasbullah H, Subhan F (2011) Indoor Child Tracking in Wireless Sensor Network using Fuzzy Logic Technique. Research Journal of Information Technology 3(2): 81-92.
- Kosmatos EA, Tselikas ND, Boucouvalas AC (2011) Integrating RFIDs and Smart Objects into a Unified Internet of Things Architecture. Journal of Advances in Internet of Things 1(1): 5-12.
- Ning Y, Zhong qin W, Malekian R, Ru chuan W, Adbullah AH (2013) Design of Accurate Vehicle System using RFID. Elektronika ir Electrotechnika 19(8): 105-110.
- Atzori L, Iera A, Morabito G (2014) From “Smart Objects” to “Social Objects”: The Next Evolutionary Step of the Internet of Things. IEEE Communications Magazine 52(1): 97-105.
- Fortino G, Guerrieri A, Russo W, Savaglio C (2014) Middle wares for Smart Objects and Smart Environments: Overview and Comparison. Internet of Things Based on Smart Objects P: 1-27.
- Ibrahim B, Mukhtar JI (2016) Changing Pattern of Prostitution: An Assessment of Transnational Commercial Sex by Nigerian Women. ESJ 12(2): 81-95.
- Liu X, Baiocchi O (2016) A Comparison of the Definitions for Smart Sensors, Smart Objects and Internet of Things. 2016 IEEE Annual Information Technology, Electronics and Mobile Communication Conference P: 4.
- Awolusi AB, Akinyokun OC, Iwasokun GB (2016) RFID and RTLS-Based Human Resource Monitoring System. British Journal of Mathematics and Computer Science 14(4): 1-14.
- Akinyokun OC, Akintola KG, Olabode O (2016) Real-Time Whole-Body Action Recognition in Videos using Threshold Hidden Markov Model. Journal of Mathematical Sciences of the National Mathematical Centre 4(1).
- Abdulkabir OS (2017) Causes and Incisive Solutions to the Widespread of Kidnapping in Nigeria Current Administration: Under Scholastic Scrutiny. J Pol Sci Pub Aff 5(2): 258.
- Gladysz B, Santarek K (2017) An Approach to RTLS Selection. Proceedings of 24th International Conference on Production Research (ICPR 2017).
- Akinyokun OC, Akintola KG, Iwasokun GB (2017) A Framework for Combating Human Trafficking and Kidnapping using Smart Objects and Internet-of-Things. Proceedings of the Second International Conference on Applied Information Technology (AIT 17) P: 9-15.
- Adewole DB, Akinyokun OC (2020) Workplace and Human Resource Safety Monitoring using Internet of Things. Journal of Artificial Intelligence Research 10(1): 64.






























