A Process Mining Support for Product Line Configurations
Houssem Chemingui*
University of Paris I-Panthéon Sorbonne, Centre de Recherche en Informatique Paris-France
Submission: October 29, 2020; Published: November 23, 2020
*Corresponding author: Houssem Chemingui, University of Paris I-Panthéon Sorbonne, Centre de Recherche en Informatique Paris-France
How to cite this article: Houssem C. A Process Mining Support for Product Line Configurations. JOJ scin. 2020; 2(2): 555584.DOI: 10.19080/JOJS.2020.02.555584
Abstract
Considering previous experiences and analyzing user traces can provide knowledge and improve product and product line configurations. For thus, mining the appropriate processes becomes crucial. These processes can be difficult and complex to manage dealing with a large number of decisions. In the context of product lines, looking for the user’s best configuration alternatives, leading with satisfying and optimized experiences, can have an added value and be important. The users make choices by selecting variables according to their needs in an interactive and iterative way. Extracting user traces when they are making interactions becomes possible. Then, mining the configuration process according to the obtained logs seems interesting. This paper aims to introduce how to overcome configuration problems with a process mining support
Keywords:User traces, Product line configuration, Complex, Process mining support
Motivations and Challenges
Considering the context of the automotive industry, today, most car brands offer an online configurator for their customers. The customer finds a tool on the website of the brand that allows him to configure a customized car according to his choices. In reality, behind the proposed choices, there is a product line model [1,2] that gathers all the possible choices that can be made by the user with taking into account the technical constraints. For example, if the user chooses a sports car, the motorization has to be powerful (> 10 horsepower for example), and the wheels have to be wide. On the other hand, several choices have to be made by the user that make the task of configuration that consumes a lot of time. The advantage of mining [3] the old configurations is making it possible to improve the next configurations and guiding the user’s choices. Let us suppose a car configurator which is able to know what are the best-selling cars in 2016? Which cars are most purchased by women? What are the best-selling cars in Africa? Which cars are best sold by young people? Which cars are full options? What was the last car that an x client configured? Which customers have the same intentions? Which cars have always been sold? Which cars have been configured several times but have not been purchased? Which customers were serious and what did they buy? Which cars have been configured with maximum manual choice of users? Which cars have been configured with maximum propagation of technical constraints? Which choices to provide for the user in the first place for a better experience? Which choices order to provide for the user when he is configuring a new automobile? What are the cars configured with too many configuration steps and too much charge for the solver? Which cars have been configured quickly? Which choices should not be provided to customers? Which choices allow the company to earn in human resources (in car assembly for example)? Which choices make it possible to configure a car with the lowest cost for the company? How do you push the user to configure a car that costs the least for the company? The profit seems to be well shared between the customer and the company. The customer will be faced to an easier configuration task and the company succeeds in retaining its clientele in a more pleasant and profitable context. In a more general context, we need to have a global and a detailed view of the previous configurations. The interpretation of these experiences can contribute to guide configuration processes to lead to a satisfying product guided by traces. Several guidance artefacts can be produced through process mining such as fashionable products, serious users, lost configurations, best sellers, worst sellers, safest configuration paths, rapid configurations, flexible configurations, customized configuration, full options products, etc.
Approach for Mining Product Lines
Configuration Processes
As shown in Figure 1, the proposed approach has to support main components, notably a front office and a back office. The front office is a visible part for the users which obviously offers to them a space for the product line configuration. The back office is a set of operations that go behind the scenes (not visible to users) when guiding directives. In the back office, there are mechanisms that occur in order to record events and transactions between users and the proposed system. All the users’ traces have to be considered and recorded in logs by a log extractor process. The purpose is to import these logs and analyze models, throw indicators and measures by process mining techniques. These analyses have to be interpreted to provide knowledge and guidance indicators. Each mechanism of the approach constitutes at the same time an independent and cooperative element with the whole. Both, the logs extractor and the process miner handle with traces, rules, metrics, indicators and knowledge.
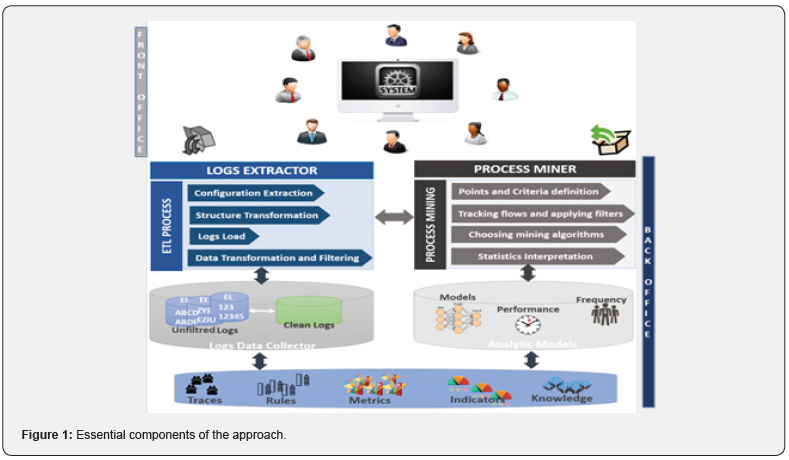
Logs Extractor
The “Logs extractor” component generates an ETL (Extraction, Transformation, and Load) process. The first step is the extraction of configuration traces made by users. A transformation of the traces structure and a filtering of the data is important but according to intentions [4]. Throughout the ETL process there will be continuous learning. We start from unfiltered logs as they are. A conversion of formats with a filter application makes it possible to duplicate repetitions and uselessness in order to capitalize transformed and relevant logs. As information that we can capture during the configuration process, we can cite the username, age, gender, the feature selected, the feature rejected, the feature decision step, configuration duration,
Process Miner
The second component is the “Process Miner”. Mining past product lines configuration processes is mainly based on logs transformed following an ETL process. Throughout the process mining, a definition of criteria is defined. Monitoring flows and relationships is also commendable. The choice of process mining algorithms depends on the desired intentions and ends. Transformed traces will be considered as the parameters of the process mining algorithms. The outputs of these algorithms are statics, models, rules and flows that should be interpreted to produce knowledge and guidance metrics.
Conclusion
Process mining has proved a powerful way for improving many processes in many domains, such as education, catering, airports, pharmacy, etc. Our proposal is mining previous product line configurations and listening to users’ actions when they are configuring a product from a line in order to enhance their future configuration processes. We believe that our approach is beneficial as it is an explicit attempt to use the process mining in the context of product line engineering. However, further work is and will be completing this proposal. Actual work focuses on the events logs extraction and proposes structuring information that have to be considered and captured; analysis must be based on a larger sample of configurations and from different user profiles. A next step is to translate the process mining outputs into referral techniques that guide users and provide them a better experience. Recommendation guidelines [5,6] have to be automatized according to the process mining analysis.
Acknowledgements
This work is supported by the French–Tunisian CMCU project 16G/1416 called CONFIGURE.
References
- Pohl K, Böckle G, van Der Linden FJ (2005) Software product line engineering: foundations, principles and techniques. SpringerScience & Business Media.
- Clements P,Northrop L (2002) Software product lines. Boston: Addison-Wesleypp. 226-229.
- Van Der Aalst W (2012) Process mining. Communications of the ACM 55(8): 76-83.
- K Kang, S Cohen, J Hess, W Novak, S. Peterson (1990) "FeatureOriented Domain Analysis (FODA) Feasibility Study". Technical Report, Carnegie-Mellon University Software Engineering Institute.
- Shen GB, Li S (2009) U.S. Patent No. 7,599,918. Washington, DC, U.S. Patent and Trademark Office.
- Robillard M, Walker R, Zimmermann T(2009) Recommendation systems for software engineering. IEEE software 27(4), 80-86.






























