Biometric Techniques: A Mini-Review
Huang L1* and Xinzhe C2
1Department of Engineering technology, Metropolitan State University of Denver, USA
2Department of computer Engineering, Colorado State University, USA
Submission: January 31, 2018; Published: April 02, 2018
*Corresponding author: Lin Huang, Engineering and Engineering Technology, Metropolitan State University of Denver, USA, Email: lhuang1@msudenver.edu
How to cite this article: Huang L, Xinzhe C. Biometric Techniques: A Mini-Review. Eng Technol Open Acc. 2018; 1(3): 555562. 10.19080/ETOAJ.2018.01.555562
Abstract
Biometrics is the body measurement and statistical analysis of people's unique biological traits. It has been applied for identification and access control. This mini-review paper will provide you with comparison of the biometric technologies based on different biological traits for identification and authentication. In addition, this paper also discusses the challenge and controversy in the area of biometric person recognition.
Abstract: Biometrics; Recognition; Security; Technology
Introduction
With the development of Engineering and Technology, it is becoming extremely important and critical to reduce the threats in privacy, personal safety and public security in 21st century. Biometrics is the technology of measuring and analyzing biological data of human subjects involved for person authentication or identification purposes. Its progress in recent years has brought in many civilian, military and government applications. It is believed that biometric technology is the most ideal solution to ensure the security and privacy of our personal information, and let us have confidence in identification systems [1].
Biometrics apply for different biological traits, such as fingerprints, irises, retinas, signatures, voices, faces, etc. (Figure 1) to recognize a person [2]. There are many debates about the merits and demerits of different biometric systems. This paper presents the description and advantages/disadvantages of the most popular ones listed in Table 1.
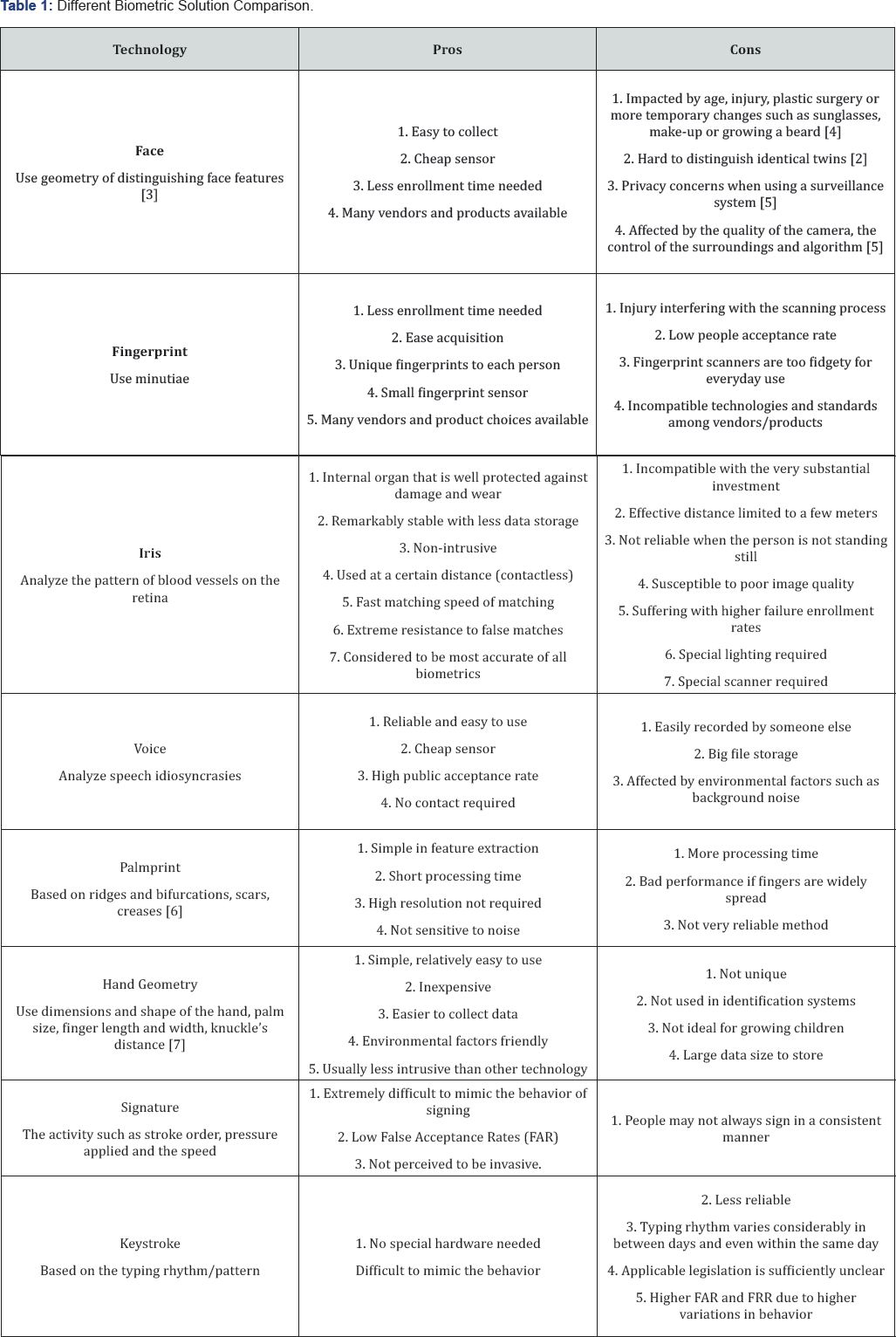
Discussion
Biometric solution can be applied for a wide range of security areas, including access control, time and attendance management, surveillance, and boarder control, etc. Among those solutions, face recognition has been used in projects to identify card counters or other undesirables in casinos, shoplifters in stores, criminals and terrorists. Fingerprint recognition has been applied in US-VISIT program [8]. IAFIS system with over 47 million subjects is maintained by the FBI Criminal Justice Information Services (CJIS) and includes automated ten-print and latent fingerprint search. The Canada-US Fast Track Nexus program utilizes iris recognition to manage frequent travellers to pass through boarder.
Biometric solutions are also facing challenges. The use of biometric data might be compromised by any unauthorized party and used for other purposes which are different from the original consents or agreements. Another risk is that the biometric data can be captured during their transmission to the central database and fraudulently replicated in another transaction.
The challenge of biometrics also includes how to develop and commercialize the systems by addressing all needs for biometrics and achieving all potential benefits. Moreover, the system should work for everyone and everywhere with 100% accurate rates under all kinds of conditions and environments. Data storage should also be small with fast recognition speed. It is a tough job.
References
- Li, Stan Z, Jain AK (2015) Encyclo pedia of Biometrics, (2nd edn), Springer, New York, USA.
- Nagpal R, Nagpal P, Malhotra S (2012) "Biometric Techniques and Facial Expression Recognition-A Review”, Journal of Global Research in Computer Science 3(11): 69-76.
- Park U, Tong Y, Jain AK (2010) 'Age Invariant Face Recognition”, IEEE Transactions on Pattern Analysis and Machine Intelligence 32(5): 947-954.
- Deb D, Best Rowden L (2017) Jain AK "Face Recognition Performance Under Aging”, in CVPR, Workshop on Biometrics, Honolulu, HI, USA .
- Huang L, Zhuang HQ, Morgera SD (2009) "A method towards face recognition”, International Journal of Intelligent Systems Technologies and Application 7(3): 282-295.
- Jain AK, Feng J (2009) "Latent Palm print Matching”, IEEE Trans. PAM1 31(6): 1032-1047.
- Jain AK, Nandakumar K, Ross A (2016) "50 years of Biometric Research: Accomplishment, Challenge & Opportunities”, Pattern Recognition Letters 79: 80-105.
- Documents, Palm Print Recognition 121-127.






























