Transverse Zone: Explanation and Definition in Comparison with Comfort Zones
Nadine Touzeau*
Profiler, Net-Profiler-Behavioral and Environmental Analyst-Researcher, ACFE USA Member, Paris, France
Submission: May 09, 2018;Published: May 23, 2018
*Corresponding author: Nadine Touzeau, Profiler, Net-Profiler-Behavioral and Environmental Analyst-Researcher, Paris, France, Tel: 33641197673; Email: nt.profiler@gmail.com
How to cite this article: Nadine Touzeau. Transverse Zone: Explanation and Definition in Comparison with Comfort Zones. J Forensic Sci & Criminal Invest. 2018; 9(1): 555753. DOI:10.19080/JFSCI.2018.09.555753.
Abstract
Man in real space behaves in different ways depending on the person in front of him. They may have a desire to flee the person or to get closer to them. He may want to talk with or without it, trust him or not, see her again or not. The desire to communicate more, to know more, to see each other again, or on the contrary that the exchange stops quickly, that the relationship stops, will depend on the feeling, the alchemy, the synchronization between two people. Thus, a physical distance may be closer if you feel the urge to get closer or be attracted to a person. On the other hand, the distance will go away if you feel uncomfortable or in phase with the person. This is how we discovered and delineated the “Comfort Zone” [1]. The comfort zone allows any person and any element that reassures, that we know, that does not allow us to ask questions, that makes us feel secure. Challenging or changing is not easily accepted in this area. Routine, fluency, knowledge and control are appreciated. If we rely on the fact that we consider that there are three zones of distance or psychological according to several researchers, as the one of which is Hall [2].
With “Proxemia” (Hall, 1963), these physical distances with others go from the physical proximity going from close to his body. We are there in real space with physical relationships in a universe of matter of all kinds, palpable, fragrant, that we can touch, move in a space around ourselves. As I mentioned in two of my previous publications [3]. In virtual space, the approach is different. Virtual space modifies these comfort zones, considering that the person acting in virtual space lives in reality. This explains behavioral differentiations with behaviors practiced in the virtual, reproduced in the real world. A complicity that makes it more difficult to contain cybercrime in order to understand and apprehend the Hats more quickly. This is the subject of one of my three theories, “Transverse Zone”. My other two theories “Avatarization” and “Virtual Intelligence” are inseparable from the “Transverse Zone”, developed also in my book”Net-profiling: Behavioural analysis of cybercriminals “. (Touzeau, 2015)
Keywords: Net-profiling; Transverse zone; Cyber criminality; Behavioral differentiation; Avatarization; Virtual Intelligence
Introduction
We use to live what is easy and comfortable for us. We feel secure when we do something knew, something understand, something integrate in our way of life. Our behavior is relaxed, without stress. We act without asking themselves questions [4]. Our senses are in action: hearing, sight, smell, touch, taste. It is part of our nature to activate these senses that have been used for generations and are part of what guarantees our equilibrium in order to evolve in everything that makes our life. Whether we are flying, scuba diving, speleologist, traveling in space, it requires us to rely on certain senses more than others and reinforce or even multiply behaviors’ tenfold. In virtual space, the same is true while creating new behaviors’. The virtual allows you to get almost everything you want without moving by simply using an internet connection.
The simple fact of not having to move, of not taking too much energy and of obtaining in a thousandth of a second what in reality sometimes requires months, or remains inaccessible, obliges to use such a facility without limit. Our behavior towards the connected object changes the way we behave, the way we live and even our relationship with what surrounds us, whether it be our loved ones, such as equipment, such as work, sport or travel. Our behavior towards the connected object changes the way we behave, the way we live and even our relationship with what surrounds us, whether it be our loved ones, such as equipment, such as work, sport or travel. It is on these overlapping behaviors, different between the real and the virtual, that I developed my theory of the “Transverse Zone” that I use in my job as a net-profiler.
Methodology
The analysis was done by me on a panel of virtual addicts, hackers and cybercriminals. Information collection was identified and analyzed. Then a questioning was carried out and cross-checked with the analyses. When I showed my “Transverse Zone” theory, they all recognized themselves in it.
Zone Transverse Definition
The “Transverse Zone” defines the behavior of virtual addicts, hackers and cybercriminals using a connected tool in their daily lives. This space located in the real space is part of the integration, appreciation and enhancement of the universe that surrounds benevolent or malevolent people who cannot do without their connected tool (Smartphone, tablet, etc.). The “Transverse Zone” makes it possible to understand the mode of operation of these profiles, whose behavior adapts to the addition of the connected tool in their personal and professional life. This induces different behaviors in real space, also coming from virtual space, a transversal universe. The behavior in real space with this connected tool changes in order to keep the contact most often with the connected tool and to adapt its life around this connected tool [5]. The emotional and the affective lose ground on the need to live with and for the contribution that the connected tool provides to these profiles. The behavioral differentiation found in the “Transverse Zone” complements other differentiating behaviors between the real and the virtual, such as “Avatarization”.
Discussion
When you are on your sofa choosing a dress, buying it online and ordering it, your relationship with shopping that you did before is no longer the same. It’s the same for a cybercriminal. An offender who acts in real space undertakes to take risks by showing himself in order to identify the information and elements necessary to properly commit his crime or offence (except for compulsive offences). This offender, even masked, gloved; cautious on several points takes the risk of being recognized in various ways ranging from DNA to a video. It also requires energy that can generate stress, adrenaline, fear, sweat. It also requires time, a time that can sometimes be long depending on the location, the timing chosen to steal or kill. It also requires a material need that can be cumbersome, depending on the offence to be committed. About cybercriminals, « such crimes are less likely to be caught and prosecuted [6] only about 5% of cyber-criminals are caught» (Kshetri, 2009) When the cybercriminal acts behind his connected tool, he does not take the risk of physically putting himself forward in a sometimes unknown geographical area Figure 1.
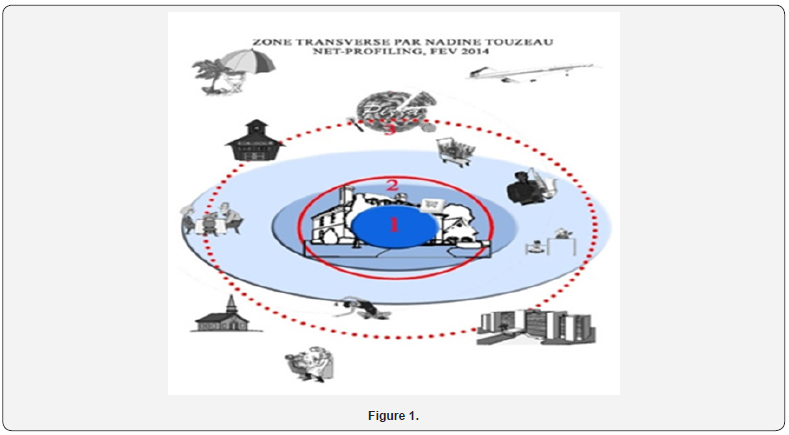
He doesn’t risk being seen as a person knowing that he can also be recognized. This hat no longer takes the risk of putting itself in danger and having to control its fears and emotions. He will act behind a screen towards targets that he will choose according to his objectives. Moreover, the word cybercrime is mentioned, but crime in the literal sense of the term is extremely rare in the virtual world or more associated with collateral damage as a result of having been the victim of a cyber attack. He will therefore be in a comfortable and reassuring element feeling protected by the fact of being an actor behind a screen. Especially since he will have taken all the steps, in principle, not to be spotted, such as helping himself to add Proxy to better hide. In the comfort zone, we consider that the comfortable and reassuring element is often his house, even his room, environments that are usual and known to us that we appreciate. The cybercriminal constantly needs his connected tool in order to be reassured. Being a person living in real space, his comfort zone remains but will undergo some modifications according to his profile, his needs and his desires. If the cybercriminals were to force them to have lunch with the family every Sunday, they would tend to move away or feel uncomfortable and help themselves manage this situation using their connected tool that would reassure them in order to be informed and act according to what is necessary.
If the cybercriminal devotes him to sport, he will favour the practice of it in his own personal universe which can perfectly be summed up in a large room dedicated to his connected tools and spaces meals, nights and hygiene. As his perception of a comfort zone changes, he will create his new comfort zone which will revolve around a single universe: his connected object and/or his room with his connected objects. The virtual does not have the same space time as the real. First because you can have everything in one click anywhere on the planet. Then because, in fact, other cybercriminals act so quickly in order to reach their end. Finally, because the life rhythm of their target must be analyzed, including from the target’s entourage, in order to obtain the maximum information to better act against them, but also to protect themselves from them. This space being transversal since the connected object follows it everywhere; this is the reason why I named it “Transverse Zone”. It should be noted that without the connected tool, the cybercriminal can quickly panic, feel disarmed, lost, and therefore no longer feel comfortable. Even in the comfort zone. While anywhere on earth, as long as he has his tool connected, the cybercriminal will be more confident and serene, even if the comfort zone is at level 2 or 3. I made a diagram of the “Transverse Zone” to illustrate my words. As I explained, we see in this diagram that the “Transverse Zone” includes zone 1, but does not have the same assessment of the boundaries of zone 2 and 3. That’s according to the cybercriminal profile.
Conclusion
While 73% of Internet users say they “can no longer do without the Internet in their daily lives” (IFOP, February 2012), their behavior towards this technology shows multiple contraditions and ambiguities [7]. These contra-dictions and ambiguities range from insecurity to how to behave behind the connected screen. According to my own research and field results, we know that cybercriminals did not detach themselves from their connected object. What had to be noticed, however, was that his behavior changed because of this connected element that almost never leaves him. Everything revolves around him as well as the way of living and behaving of the cybercriminal [8]. This also complicates the way cybercriminals are apprehended in real and virtual space and thus makes investigations longer.
Without integrating this notion, the other theories I have developed concerning the behavioral differentiations between the real and the virtual, namely “Avatarization” and “Virtual Intelligence, it is difficult to under-stand cybercriminal is to make predictions in cyber defense. The virtual allows many behavioral changes in this space that sometimes happens in reality. The “Transverse Zone” is an example since the so-called comfort behavior cannot be applied for a cybercriminal because everything revolves around his connected tools. In the real world too. The net-profiling allows detecting these behavioral differentiations between the real and the virtual. An essential profession in the face of the behavioral differentiation between the real and the virtual for better investigation.
References
- Alasdair White (2009) From Comfort Zone to Performance Management: Understanding Development and Performance.
- Proxemia is an approach to the relationship to material space introduced by the American anthropologist Edward T. Hall in 1963.
- Touzeau N (2017) Behavioral Cybercriminals Differentiations between the Real World and the Virtual Space. J Forensic Res 8(6): 401.
- Touzeau N (2018) Criminal and Transposition of modus operandi from the real to the virtual using several signatures: Case of “the drowned of the Garonne” serial crimes in France. Journal of Forensic Science.
- Touzeau N (2018) Avatarization, Another Way to Understand Cyberbullyers Behaviour in the Real and the Virtual Worlds as Described by Net-Profiling. Journal of Cognitive Neuropsychology 2(1).
- A proxy is a computer software component that acts as an intermediary between two hosts to facilitate or monitor their exchanges. In the more specific context of computer networks, a proxy is then a program used as an intermediary to access another network, usually the Internet.
- Nir Kshetri book Positive Externality, Increasing Returns, and the Rises in Cybercrimes ». He is Professor at Bryan School of Business and Economics, The University of North Carolina-Greensboro (UNCG). He is a research fellow at Research Institute for Economics & Business Administration - Kobe University, Japan.
- Jean François Lemoine, book In search of a better understanding of Internet users’ behavior.






























